ICT Solutions
-

IPTV Solutions
An IPTV system deployed within a business enables hundreds of channels of TV and video to be viewed on an unlimited number of TVs and PCs connected to your existing data network. IPTV delivers television content using IP signals rather than traditional, terrestrial satellite signals. A particular form of transmission known as IP multicasting is used to minimize the demand on network bandwidth. TVs are connected to your network by a small IP Receiver controlled using an infrared remote control handset. PC users do not require any additional hardware and select channels using a control panel displayed on the PC screen. We offer a full set of IPTV components including DVB-Gateways, (DVBS2, DVBT2, DVBC), several levels Middleware, Linux and Android Set Top Boxes and Smart TVs.
-

Interactive Solutions
Interactive solutions allow you to engage with your audience in extraordinary ways. Information can be displayed, captured, manipulated, and shared quickly and easily. Whether it’s for your meeting room, lobby, classroom, command center, courtroom, or training facility, interactive solutions offer a level of engagement and excitement unlike any other.
We can help you create an inspiring and enriching interactive environment in any space. We offer quality interactive panels, both with multi-touch and multi-write capabilities, to optimize participation and interaction. Our handheld devices such as Chromebooks and interactive PC’s, make for a completely mobile and cost-effective collaboration solution. It’s never been easier to bring interactivity to life!
-

Meeting Room & Class Room Solutions UAE
Today’s demands for idea sharing and collaboration are changing more rapidly than ever. From the modern-day conference room to today’s evolving classroom, there’s a greater need for the right technology solutions. TCT provides integrated solutions to help meet these challenges and to solve modern-day collaboration needs. From video distribution and collaboration to room book, control, and infrastructure needs, We provide the solution expertise coupled with the product portfolio to build a solution that fits your needs.
TCT aims at providing engineering support for the A/V equipped conference rooms and classrooms. Today’s demands for idea sharing and collaboration are changing more rapidly than ever. From the modern-day conference room to today’s evolving classroom, there’s a greater need for the right technology solutions. TCT provides integrated solutions to help meet these challenges and to solve modern-day collaboration needs. From video distribution and collaboration to room book, control, and infrastructure needs, we provide the solution expertise coupled with the product portfolio to build a solution that fits your needs.
Aspects that TCT covers while providing meeting room and classroom solutions:
Design and implementation: We provide expert advice and coordination in each step of implementation of classroom and conference rooms designs. The staff of our team works with the users to help them understand the requirements of the system. They help in understanding the need for hardware, software, and physical layouts that will be required to incorporate the solutions. We work in complete coordination with the users to design and install the services.
Life cycle upgrades and replacements: we are committed to our customers and thus assist them with life cycle upgrades and replacements for the A/V equipment installed in the rooms. We formulate an upgrade plan that is based on department requirements, technology changes and user-friendly.
Desktop replacement program: we at TCT handle the ordering, receiving, configuration, and set up of computer software and VIRTUALIZATION SOLUTION UAE hardware through the program of a desktop replacement.
Setting up conference phones: we are accomplished in setting up conference phones and setting up their coordination with the department to create a sync account and network for all the physical locations.
User training: we don’t just install the system and leave the user to navigate rather go a step ahead and provide basic instruction to the users and their faculty.
Periodic maintenance: we provide periodic checks of the system for its smooth functioning.
-

Digital Signage
We offer digital signage and screens which let you deliver an instant message to your customers. These solutions enable you to easily update the content and save on printing costs. Digital screens are useful tools for communicating information and promotions especially at points of sale.
Digital or dynamic signage is a specialized form of slivercasting in which video or multimedia content is displayed in public places to serve informational or advertising purposes in an effective and interactive way.
-

Public Address
Our PA solutions are best suited for large organizations such as schools, hospitals, shopping centers, airports and facilities that need to make announcements or declare states of emergency. Public Address systems are highly effective and low cost methods of communicating information to a large area or group of individuals quickly. We design, implement, test, and handle the maintenance of systems, from simple microphone and speaker arrangements to full evacuation systems based on a thorough assessment of the client’s needs.
-

Backup Solutions
Backup software is primarily used as a means of securing important data residing on computer or server hard drives. It can be used for individual computers or for an enterprise’s computers, servers and networking devices. Backup software for individual use generally backs up selected files, folders and important operating system files on the same computer/hard drive. The advanced or enterprise-level software is typically integrated within each computer, server or node and backs up selected files and folders on a scheduled basis or as required. The backup software transmits the duplicated/backup data over the network/Internet to a local backup server or on an Internet/cloud-based backup storage server. Backup software also has the ability to compress data to reduce the amount of backup space required, as well as versioning control for maintaining different versions of the same file.
-

Virtualization Solution UAE
Virtualization can increase IT agility, flexibility, and scalability while creating significant cost savings. This method replicates the behavior of specific software components in cloud-based and API-driven applications, most useful in product or service testing.
ICT solutions UAE provides a platform where happenings of servers are not tied to a specific piece of physical hardware and allow multiple virtual workloads that can be done on the same machine. The first and foremost benefit of Virtual visualization is that it increases server utilization rates in the data center and decreases the costs but then this is just a small part of the big and crucial benefits that it can provide. Some of the benefits that virtualization can provide by being a revolutionary technology as developed by TCT solutions UAE are as follows:
Reduced hardware costs – virtualization solutions by means of cloud computing approach, helps in optimum utilization of the hardware as one physical server can now hold multiple virtual machines.
Faster server provisioning and deployment – virtualization as a service provided us enables your system provisioning and deployment within a very short span of time like some minutes. Time and costs add up and with virtualization, the same work is more time consuming and grueling. For data resources explosion there is the requirement of virtualization.
Much better disaster recovery – the most important benefit of virtualization as provided by TCT is that virtual machines can very easily move from one server to another. We have enhanced feature whereby the software helps to automate the failover during a disaster.
Increased productivity – with lesser physical servers there is a limited expense on servers and thus the cost of maintenance reduces considerably.
Virtualization can increase IT agility, flexibility, and scalability while creating significant cost savings. This method replicates the behavior of specific software components in cloud-based and API-driven applications, most useful in product or service testing. Virtualization thus brings positive transformation.
-

Storage (NAS & SAN)
We offer networked storage solutions that help your business save on costs and improve its interconnectivity, based on your company’s specific needs.
Our solutions are designed to meet the capacity, performance and availability requirements of all your business applications whether those applications sit inside virtualized or non-virtualized environments. It is simply a matter of time before every small business grows and requires more space for data storage. Information is the lifeline of most companies and investing in new applications that manage and protect data can be complex and expensive.
Network-Attached Storage. : Network-attached storage (NAS) provides fast, simple, reliable access to data in an IP networking environment, serving files by its hardware component, software, or configuration. NAS solutions are suitable for small and medium businesses that require large amounts of economical storage shared between multiple users over a network. NAS systems are networked, purpose-built specialized computer appliances that are easy to manage and do not require extensive IT support, often lacking at smaller companies. And given that many small businesses lack IT departments, NAS solutions are easy to deploy, centrally manage and consolidate.
Storage Area Network : A SAN reorganizes storage in the common user network into an independent, high-performance network, known as block level data storage. SANs are primarily used to enhance traditional storage devices. They are typically assembled using three principle components: cabling, host bus adapters (HBAs) and switches. Each switch and storage system on the SAN must be interconnected and the physical connections must support bandwidth levels that can adequately handle peak data activities.
-

Proxy Solutions
Our extremely fast, secure and highly private anonymous proxies offer proxy services which IPs can originate from various countries.
We offers highly anonymous, secure private proxy services which use SSL and other enhancements to ensure experience is the fastest available and is also extremely secure.
We offer full support which includes FAQ, proxy configuration guides, robust knowledge-base and live support staff. We make sure that you are happy with our proxy services.
-

Unified Threat Protection
Unified threat management enables organizations to implement multiple layers of protection without the complexity of several independent devices and management consoles. Some functions that may be included in UTM solutions include next-generation firewall, web content filtering, email antivirus and anti-spam, web application firewall, and endpoint security management.
-

Endpoint Protection UAE
Every endpoint is a launch pad for a cyber attack, no matter how it touches your network. Our multi-layered endpoint protection provides everything from file reputation and behavioral analysis to advanced machine learning AI.
Our endpoint protection suites emphasize integration, automation, and orchestration as the foundation of the threat defense lifecycle. It harnesses the power of machine learning to detect zero-day threats in near real-time and streamlines the ability to quickly expose and remediate advanced attacks.
With its bendable, encrusted structural design, Telephony Security for Endpoints renders the unsurpassed protection against complicated coercion without finding the middle ground on performance.
Unlike the traditional Endpoint Security and professed Next-gen AV, At Telephony, we employ a blend of our original machine cultured technologies and the skill to scrutinize activities and conduct to identify attack plan or protocol that aids us to thwart, detect and obstruct dangers and risks.
The Endpoint Security employed by us is efficient in taking automatic actions to safeguard the running of the business seamlessly by kicking back the malevolent happenings. The significant features of Endpoint Security with a diverse approach in balancing the work performance of an enterprise and detecting the false positives are:
- Protection against ransom ware
- Detect complex constant threats
- Guarding against potential attacks
- Prevention of file-less attacks
- Put a stop to data breaches
- Cloud-based remote management
In business organizations, deploying endpoint solutions are crucial. The working members of the organizations require the data with easy accessibility. Also, the employees while performing their job activities need W-Fi networks or access to data, which makes the network security indispensable for an enterprise.
The endpoint protection we provide performs as a major security tool to safeguard the access points by maintaining comprehensive control to prevent dangerous and malicious activities.
-
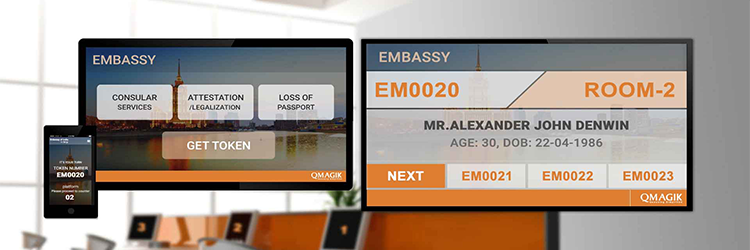
Queue Management System
A queue management system is used to organize queues of people waiting to be served at organizations such as banks, hospitals, stores, or government institutions. Our queue management systems help your organization handle online and offline traffic by providing visitors with virtual and linear queuing solutions such as pre-booked appointments, remotely ranked allocation, SMS or mobile queuing, and more.
-

Intrusion Alarm and Antitheft Alarm
Intrusion Alarm:We offer a security alarm system designed to detect intrusion or unauthorized entry into a building or specified area.
Our portfolio of security alarm systems includes intelligent detectors with false alarm immunity, keypads that are easier to use, panels with more power, and communications solutions that compensate for VoIP. Our security alarms are designed to detect intrusion or unauthorized entry into any premise. This helps protect commercial, public, and residential properties alike against burglary or property damage.
Anti-theft Alarm:We offer an anti-theft alarm system with an electronic immobilizer, offering maximum protection against theft.
Our anti-theft alarm is equipped with audible and visual warning signals that strike the attention of passers-by and deter potential thieves. Through one or multiple sensors, the alarm systems detect unauthorized entry and trigger a warning signal by alerting a home device to indicate the intrusion.
-

Security Solutions
If you have a need to protect and/or secure people and/or physical assets, we will be able to assist you. We offer a full range of surveillance, access, fire, building automation and building management solutions. Our e solutions are delivered based on your unique set of requirements. For all the solutions that we offer, we support you with design layout, installation, testing, commissioning and maintenance.
-

Gate Barriers
Barrier gates are generally used in parking lots and garages. They are also used in many commercial applications such as airports and public facilities. These units can be operated automatically by card reader, keypad, telephone entry system, or manually controlled within kiosk.
-

Access Control in UAE
We provide comprehensive physical access control solutions to secure your facilities, assets, networks and cloud resources.
Our physical access control solutions are designed to deliver sophisticated security solutions that secure your facilities, assets, networks and cloud resources.
Access control systems are common to one and all. Anything that can be secured by means of a password or has a restriction placed on its access is said to be under the access control system. Using the latest access control credentials from TCT is the next big innovation to hit the market. Biometrics and card-based alternatives had been there for a very long time but then there were shortcomings in the system and thus access control is the need of the hour. At, TCT we provide comprehensive physical access control solutions to secure your facilities, assets, networks and cloud resources.
Our physical access control solutions are designed to deliver sophisticated security solutions that secure your facilities, assets, networks and cloud resources. We provide services that are well suited as per your requirements and budget.
Mobile credentials and their importance:
People are attached to mobiles and barely lose them and even if the phone is lost the credential can be easily canceled and maintained security. Our control access system is designed in a way that it gets easier to upload and replace a new credential in the new phone if the need arises.
Choosing the best solutions for your requirements with TCT access solutions:
To manage the credentials is quite easier when done remotely. Mobile phone-based credential system will take less time in auditing cards and spend more time on constructive aspects like monitoring and interacting with the access control and security systems along with assessing the data and environment.It is value for money option as we provide exceptional services for affordable prices. Also, cards and readers are much cheaper to install and they promote the right level of reliability and flexibility making it extremely user-friendly function. Thus the complete functionality of the system is enhanced.
-

Video Conferencing
We offer a selection of high quality video conferencing systems that redefine your audiovisual communication experience. Our solutions enable you to connect teams in different locations and on multiple devices seamlessly. Our High Definition Video Conference System Technology is flexible and allows you to connect with fixed installations at any location with full visual clarity and uninterrupted voice responses. These video conferencing systems can be combined with cloud video conferencing systems that give optimal performance with the power of the cloud.
-

CCTV Solutions
We offer one of the best selections of security solutions to meet your business requirements and budget. We carry a variety of high-quality CCTV cameras, access control systems, time and attendance systems and IP cameras. Use of Closed Circuit Television (CCTV) security cameras is considered one of the best ways of preventing thefts or intrusions at homes and businesses in addition to monitoring staff or children from afar for added security. CCTV security cameras are often mounted at important establishments such as banks, shopping malls, parking lots, living complexes, etc.
-

UTM & Firewall Solution UAE
We offer the latest next-gen firewall protection to protect your business’s network from unauthorized intrusions. Unified threat management (UTM) is an approach to security management- an evolution of the traditional firewall – that allows an administrator to monitor a wide variety of security related applications& infrastructure components through a single console. The main advantage of a UTM product is its ability to centralize security and minimize complexity.
A firewall is a network security system, either hardware- or software-based that acts as a barrier between a trusted network and other untrusted networks such as the Internet or less-trusted networks, such as a retail merchant’s network outside of a cardholder data environment. A firewall controls access to the resources of a network through allowing traffic only according to the firewall settings defined by the administrator.
-

Servers
In a technical sense, a server is an instance of a computer program that accepts and responds to requests made by another program, known as a client. Less formally, any device that runs server software could be considered a server as well. Servers are used to manage network resources. For example, a user may setup a server to control access to a network, send/receive e-mail, manage print jobs, or host a website.
Some servers are committed to a specific task, often referred to as dedicated. As a result, there are a number of dedicated server categories, like print servers, file servers, network servers, and database servers. However, many servers today are shared servers which can take on the responsibility of e-mail, DNS, FTP, and even multiple websites in the case of a web server.
Because they are commonly used to deliver services that are required constantly, most servers are never turned off. Consequently, when servers fail, they can cause the network users and company many problems. To alleviate these issues, servers are commonly high-end computers setup to be fault tolerant.
-

IVR
Interactive voice response (IVR) is a technology that allows a computer to interact with humans through the use of voice and DTMF tones input via keypad. In telecommunications, IVR allows customers to interact with a company’s host system via a telephone keypad or by speech recognition, after which services can be inquired about through the IVR dialogue. IVR systems can respond with prerecorded or dynamically generated audio to further direct users on how to proceed. IVR systems deployed in the network are sized to handle large call volumes and also used for outbound calling, as IVR systems are more intelligent than many predictive dialer systems.
-

Unified Communication
Telephony Communication Technologies ( TCT) is the most secure unified communication and collaboration solution provider for government and private organization in the region. It is unprecedented in governmental communication thanks to its flexibility of communication coupled with complete protection. Meaning you can use any communication mode you like, in one application, swiftly shift from voice to chat, email or file transfer, and all at a top secret security level.
TCT offers you a secure unified communication and collaboration solution for PCs that helps you improve the productivity of your organization by uniting efficient communication with top level security and allows you to flexibly use messaging, chat, file transfers and voice conversations. This reduces or eliminates delays in your workflow and relieves your budgets by reducing travel costs. Simply integrate Telephony into your current communication infrastructure. TCT meets the specific requirements of your organization. Other than with commercial solutions, you can restrict the usage to a centrally managed group of your staff with clearly defined authorizations and privileges.
-

Call Center and Contact Center
We provide mid-market contact and call center solutions which integrate seamlessly with your existing systems. Telephony provides simplified Call Center solutions which do not require a great deal of system integration, featuring CC Supervision, CC Distribution, CC Outbound, CCIVR, CTI & integration with CRM tools.
A call center is the main hub for handling customer and other telephone calls, usually empowered with some amount of computer automation. A call center typically has the ability to handle a considerable volume of calls at the same time, to screen calls and forward them to the specific agent, and to log calls. They are standard for a number of companies, especially those that rely on high customer interaction such as logistics or e-commerce businesses.
A contact center is generally part of an enterprise’s overall Customer Relationship Management (CRM) and is typically a modern unified communications solution with specialized software that enables contact information to be routed to appropriate resources, contacts to be tracked and full customer interaction history to be gathered and managed. It serves contact with the clients beyond just through calls and is considered to be an important element in multichannel marketing, extending beyond traditional customer service.
First contact resolution in a contact center is becoming paramount in present day customer relationships.
-

IP Telephony
Through IP Telephony, we offer an established technology for delivering voice services over an existing network infrastructure. Your business can become one of the many clients enjoying the benefits of reliable user access to a range of enhanced communication and collaboration tools.
IP Telephony is our proven idea for the future of enterprise voice communications. The most obvious benefits of an IP based voice system include lower cost, more flexibility, and improved usability and manageability. By using the existing data infrastructure instead of a separate dedicated network, enterprises save time and money. IP-based voice communication equipment represents a shift to commodity computing platforms, available at significantly lower costs and that support various functions that empower enterprises. Through Session Initiation Protocol (SIP), IP Telephony supports the following functions:
Voice Over IP Phone System Unified & Differentiated Communications Simplified Deployment and Management Interoperable Open Architecture.
-

Power Solutions
We provide a range of Uninterruptible Power Supply (UPS) products, which allow systems to keep running for short time periods when the primary power source is lost and also provide protection from power surges.
We believe that in today’s world, there is no room for downtimes that result from interrupted power supplies or outages. This is why we offer a selection of UPS power solutions. For data centers, we offer UPS products that convert incoming AC voltage to DC through a rectifier, and converts it back with an inverter. UPS systems are powered by batteries or flywheels that store energy to use in a utility failure. A bypass circuit routes power around the rectifier and inverter, running the IT load on incoming utility or generator power.
-

Wireless Solutions and Services UAE
Wireless networks are used for variety of applications, enabling corporate to have complete control over its IT and communications services. These networks are used extensively for data exchange applications like ERP and Corporate e-mail etc, Video conferencing, voice and remote surveillance systems.
Wide area computer networks for business can be built using either wired or wireless technology. Wired method has been the traditional choice, but wireless technologies are gaining ground fast. Due to poor connectivity option for local loop, organizations are moving towards wireless connectivity for WAN. It is a viable option for Wide Area Networks (WAN) for following key factors.
Easy installation Availability of service in remote and poorly connected areas reliability, Performance & Security
-

Fiber Cabling
We offer installation, design, and maintenance of all aspects of OSP / ISP copper and fiber optic cabling infrastructures, which enable your business with optimal bandwidth.
Fiber to the Home (FFTH) refers to fiber optic cable that replaces the standard copper wire used in telco systems. The advantages of the FTTH is that they can carry high-speed broadband services integrating voice, data and video, and the run directly to the junction box at the office or building.
A passive optical network (PON) is a point-to-multipoint architecture and a form of fiber-optic access network for delivering last-mile connectivity without having to provision individual fibers between the hub and the end user. No powered equipment means less cost, less network management, longer reach and no need for an upgrade. A PON (Passive Optical network) uses unpowered fiber optic spitters to enable a single optical fiber to serve several customers.
We are the leading channel partner of Etisalat in the UAE, covering their outsourced technical activities related to service provisioning, fault attending, and GPON implementation projects. We have trained and deployed more than 300 specialized personnel for Etisalat projects across the Middle East.
We have the expertise and skilled staff to help our customers with all aspects of OSP / ISP copper and fiber optic cabling infrastructure. Our engineers and fiber optic specialists design, install, splice, and test all types of fiber and copper cabling. Our team is empowered with state of the art tools and equipment including fiber optic fusion splicing equipment, OTDRs, power meters and fluke cable analysis.
-

Networking
We provide cost-effective networking solutions based on your company’s capacity, usage, and general requirements.
One of the main goals of Network Management is to make operations more efficient and operators more productive. Our services help manage the network structure and supports the use of elements like VOIP, data backup, storage of information, security, and remote access.
Structured Cabling copper, fiber and telecom LAN and WAN management Network optimization, acceleration and visibility Network design and engineering, and installation of necessary equipment.
-

Structured Cabling Service UAE
We build campus telecommunications cabling infrastructure for organizations of different size, handling design, installation, and maintenance of custom structured wiring systems.
Cabling design and installation services map out wiring data centers, offices, and apartment buildings for data or voice communications using CAT 5E or CAT6 cables and modular sockets. Our installations rely primarily on horizontal cable wiring which connects telecommunication rooms to individual outlets or work areas through a patch panel connected to the main distribution facility. This helps companies centralize and control telecom connectivity within an organization. We have vast experience successfully completing projects with complicated structured cabling work and we hope to serve your company.
-

Data Center Solutions
We are dedicated to help different types of organizations who face a number of data center challenges. We empower enterprises to focus on their core competencies by delivering the right IT service levels,providing IT infrastructure quickly to support new business initiatives, reducing operational costs, lowering environmental impact and ensuring IT compliance with legislation and regulations.

